Organisations of all sizes continue to fall victim to harmful cyber attacks, with the threat level seeming to rise every year. If successful, an attack can shut down entire systems and put your data for ransom. Only earlier this year, cyber crime hit the headlines after bringing significant disruption and loss to UK retailers through the DragonForce ransomware attacks. Criminals are now working harder to devise new ways of harvesting businesses data, bank details and any other form of sensitive information – and even leveraging AI to support their tactics.
With data protection regulations ever-present and cybercrime showing no signs of slowing, understanding the nuances of modern threats is crucial. Beyond traditional malware, tactics like typosquatting, leveraging cloned doppelganger domains, and the activation of deceptive email domain extensions remain alarmingly effective. These methods exploit simple human error, making it easy to mistake malicious communications originating from near-identical domains as legitimate. Let’s delve into the ways cybercriminals are currently exploiting these deceptive domains.
What are doppelganger domains?
Doppelganger domains are clones of legitimate domains but with a very slight difference. For example, if a company email domain extension was @infinity.group.co.uk, cyber criminals could set up another very similar domain and use this email domain extension to individually target the customers of our business using @infinitygroup.co.uk. With the dot removed, it’s then easily mistaken by the recipient as a genuine email from the company and is highly likely to be responded to.

Photo credit – https://www.wired.com
How is typosquatting involved?
Imagine this scenario.
One of our employees is in a rush and emails a colleague by typing in employeename@infinitygrou.co.uk, missing the ‘p’. In most cases, the sender will be notified with an undeliverable notification. However, if www.infinitygrou.co.uk is an owned domain, the email will then be received by someone it is not intended for and the sender will remain unaware.
Should a cyber criminal own that domain missing the ‘p’, they would receive that email and then be aware of the business email format which they can then use to gain more names. They can then target several users by email with a link to a related malware.
This practice is known as typosquatting. The goal is to trick users who unintentionally mistype a URL into visiting the malicious site.
Both typosquatting and doppelganger domains fall under the umbrella of creating deceptive, look-alike domains for malicious purposes like phishing, malware distribution, and brand damage
Email fraud via doppelganger domains and typosquatting
Doppelganger domains and typosquatting are commonly used to commit email fraud, using a ‘catch all’ method. The cyber criminals wait for an email to be sent to the fraudulent domain. For example, a domain name very similar to a well-known bank or large organisation.
At this point, the cyber criminals have access to a vast amount of email address’ and can quickly reply. The reply email a customer receives will appear highly genuine as all the information is present, due to the intercepted email content being included. Cyber criminals can then engage in a seemingly innocent conversation with the customer and request confidential details, which is how email fraud is performed.
Below you can see an image example. The sender is posing as Vodafone and asking you to view your bill, but if you look the email is slightly different.
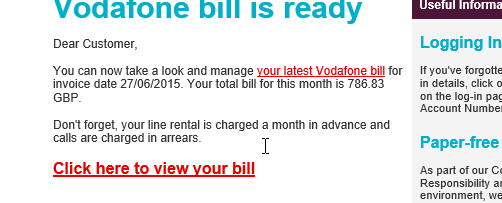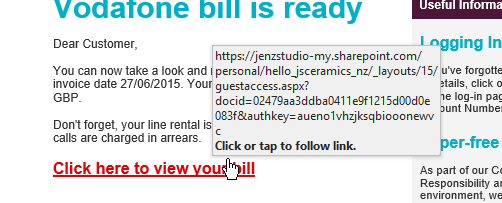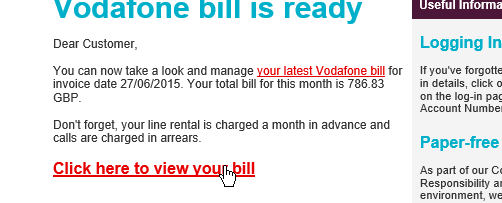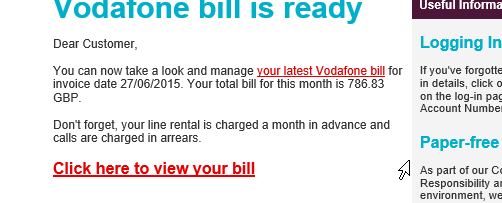
How easy is it to become a victim to doppelganger domains and typosquatting attacks?
Becoming a victim of doppelganger domain and typosquatting attacks is unfortunately quite easy due to their reliance on human error and visual deception. We often make typos when typing URLs, and our brains can easily overlook minor differences in domain names or email addresses. Cyber criminals exploit this by creating look-alike websites and emails that closely mimic legitimate services, leveraging our trust in familiar brands. These deceptive tactics are frequently employed in phishing campaigns, where a sense of urgency or social engineering can further lower our guard, making it surprisingly simple to land on a malicious site or interact with a fraudulent email without realizing the subtle discrepancies.
The effectiveness of these attacks is amplified by the increasing sophistication of cyber criminals. They continuously refine their methods to create more convincing fakes, making it harder for the average user to distinguish between a legitimate online presence and a malicious imitation. Given the high volume of online interactions and the speed at which we often navigate the internet, the opportunity for these subtle deceptions to succeed is significant. Therefore, while vigilance and awareness are crucial, the ease with which these attacks exploit natural human tendencies makes falling victim a genuine and ongoing risk in the digital landscape.
What are the implications of doppelganger domains and typosquatting on your business?
If someone in your business or a customer falls victim to one of these attacks, it can launch a cascade of other issues, including stolen information, malware or ransomware, broader attacks and more.
In this event, your business could face:
- Financial losses: This may cover data breach penalties, legal fees, recovery expenses, fraudulent payments and loss of sales
- Reputational damage: Erosion of customer trust when they become victims of scams using look-alike domains, negative perception of your security and hard work to regain customer confidence
- Operational disruption: Resources may be diverted to investigate and remediate incidents stemming from these attacks, alongside potential downtime is systems are compromised.
- Legal and regulatory ramifications: Failure to protect customer data can lead to fines and legal action under data protection regulations (e.g., GDPR). You may also take liability for damages incurred by customers due to successful attacks leveraging these deceptive domains
On top of this, if customers are targeted, they may face their financial losses and identity theft. This could harm their sentiment towards your business and prevent future custom.
Due to these implications – and the manipulative nature of these attacks – it’s crucial to act to avoid them.
How can you protect your business?
As doppelganger and typosquatting attacks rely entirely human error, it’s very hard to come up with a definite solution to combat them. However, there are many things your business can do to reduce the chances.
- Staff awareness and training: With the GDPR in play, data breaches now carry a high penalty. Make all staff aware of typosquatting email attacks so they know to look at the sender’s details before responding. Aim to give them common examples so they know what to flag.
- Be extra vigilant: Instruct staff to look at their sent box regularly and check who you’ve sent emails to. This is especially key for emails you need to manually type such as those not in your current address book. If you receive a typosquatting email, please alert the real company it’s in relation to so they are made aware.
- Use endpoint protection for devices: Ensure that all employees have an industry standard security protection put in place, through adequate endpoint protection installed across devices.
- Domain monitoring: Actively monitor for newly registered domain names that are similar to your own, including common misspellings and variations. If you are a well-known brand, you can also consider purchasing other close variants of your domain name to prevent these being brought by criminals.
- Email security: Implement robust email filtering and anti-spoofing protocols (like SPF, DKIM, and DMARC) to help prevent the delivery of emails from forged or look-alike domains.
- Incident response plan: Develop and maintain an incident response plan to effectively address and mitigate the impact of a successful attack involving a doppelganger or typosquatted domain.
Keeping your data locked down
In the event of most cyber attacks, criminals are looking to steal your data to leverage, either as blackmail, to sell on or to leverage for future attacks. Due to this, keep your data secure at all times is crucial to safety and avoiding costly breaches that harm customer trust.
In our webinar below, our seasoned experts give practical tips for protecting your data against modern risks:

