In today’s world, businesses are at a rising risk of cyber attacks. According to Microsoft data, one in three small businesses have experienced an attack, with the average attack costing around £194,875. That’s a significant financial loss if one were to hit your business.
It’s crucial to protect your business with robust cyber security practices. However, implementing cyber security requires knowledge, time and investment. It’s therefore important to focus on security projects that drive value and reduce risk the most, in line with your available resources.
Fortunately, there are several well-established cyber security frameworks designed to protect your business, following set principles. If you’re new to implementing cyber security, this can help you to create a baseline while ensuring your data is safeguarded and the attack risk reduced.
We explore the core cyber security frameworks out there, with details on how they can be applied to your business.
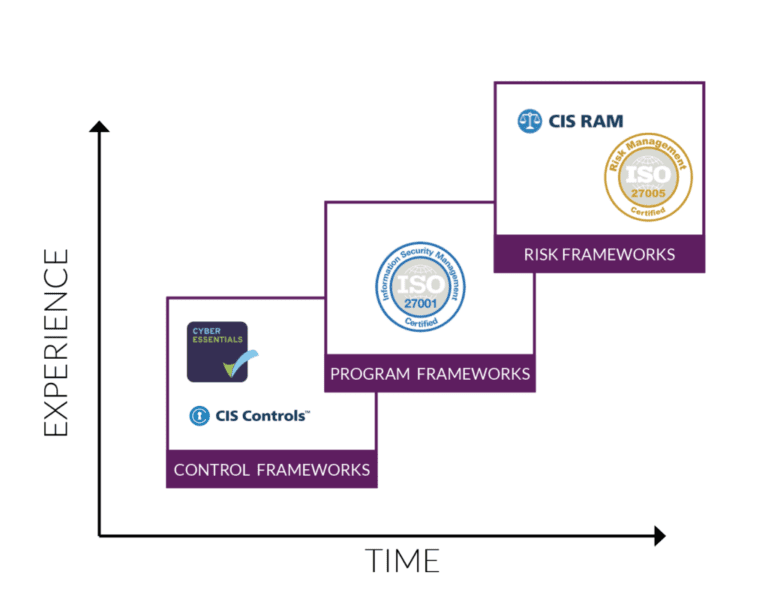
Three categories of cyber security frameworks
Cyber security frameworks come in three categories, based on how they are applied and their approach. These are:
- Control frameworks: These serve as the foundation for security programs. They consist of specific processes and measures to implement to protect against threats. Examples include access controls, encryption and monitoring.
- Program frameworks: These focus on operational aspects and governance across an organisation’s security measures. They ensure consistent implementation of controls and alignment with business goals, such as data policies and management.
- Risk frameworks: These help businesses when assessing threats, vulnerabilities and potential impacts on business assets. They help organisations prioritise security efforts based on the level of risk exposure.
Each type of framework will require a different level of effort and experience to enact. Control frameworks tend to be easiest, while risk frameworks are hardest.
Control frameworks
There are two well-known cyber security control frameworks that businesses typically utilise. These are Cyber Essentials and CIS Critical Security Controls.
Let’s dive a little more into each framework’s compliance requirements.
The Cyber Essentials scheme
The simplest framework to achieve in your business is Cyber Essentials. This government-backed framework protects data and programs on networks, computers, servers and other elements of IT infrastructure.
Cyber Essentials is a self-assessment option that assures protection against a wide variety of the most common cyber attacks. There is also Cyber Essentials Plus, which involves an external vulnerability scan and a test from a third-party certification body.
An initial audit will help ascertain whether the organisation has the necessary measures in place to defend itself against the most common forms of cyber attacks. You can then go through the self-assessment and, if you pass, you’ll receive a certificate to showcase your proven cyber security standards.
Attaining certification in either Cyber Essentials or Cyber Essentials Plus (for advanced compliance) requires that five key controls are implemented:
- Secure internet connection
- Secure devices and software
- Controlled access to data and services
- Protection from viruses and other malware
- Up-to-date devices and software
Cyber Essentials is widely recognised, meaning it can help you boost partner and customer trust while securing your business against cyber risks. In addition to mitigation against phishing and most types of hacking, UK Cyber Essentials is a partial means of supporting the ISO 27001 certification.
Find out more about Cyber Essentials in our dedicated guide.
CIS Critical Security Controls
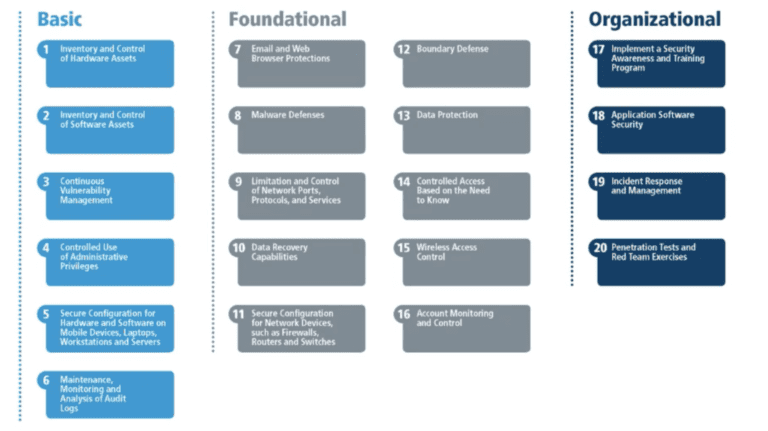
The CIS Critical Security Controls framework encompasses all the elements of Cyber Essentials, plus a prescriptive, prioritised set of cyber security best practices and defensive actions. These can help prevent the most pervasive and dangerous attacks, and support compliance in a multi-framework era.
Actionable best practices for cyber defence are formulated by a group of IT experts, using the information gathered from actual attacks and their effective defences.
The CIS controls provide specific guidance and a clear pathway for organisations to achieve the goals and objectives described by multiple legal, regulatory and policy frameworks.
These are the pillars of the CIS framework:
There are some questions to consider to ensure you abide by the framework:
- Do we know what is connected to our systems and networks?
- Do we know what software is running (or trying to run) on our systems and networks?
- Are we continuously managing our systems using “known good” configurations?
- Are we continuously looking for and managing “known bad” software?
- Do we minimise risk by tracking the people who can bypass, change, or over-ride our security defences?
- Are our people aware of the most common threats to our business or mission, and what they can do about them?
By answering these questions, in line with the CIS Controls principles, you can secure your business better against cyber threats.
Program frameworks
A program framework is the next step up from implementing controls. They drive governance across your organisation, giving you a consistent approach to data protection and risk mitigation.
There is one core program framework that is internationally recognised: ISO 27001.
ISO 27001
ISO 27001 provides requirements for an information security management system (ISMS) that protects sensitive data. It’s best-practice approach helps organisations manage their information security by addressing people, processes and technology.
Software development companies, cloud companies and IT support companies will implement ISO 27001 to assure clients that they can certifiably safeguard their information in the best possible way.
The basic goal of ISO 27001 is to protect three aspects of information:
- Confidentiality: only the authorised persons have the right to access information
- Integrity: only the authorised persons can change the information
- Availability: the information must be accessible to authorised persons whenever it is needed
Because ISO 27001 certification demonstrates robust security practices, certified organisations often find that their client relationships and retention is improved by this investment.
In addition to improving how an organisation is perceived by clients, suppliers and other stakeholders, ISO 27001 certification benefits an organisation’s internal systems, structure and daily processes.
In summary, it provides a clear framework that addresses information security risks, management processes and key operational elements. This includes how IT systems must be kept up-to-date, anti-virus protection, data storage and back-ups, IT change management and event logging.
Risk frameworks
Risk frameworks require the most effort and experience to apply. They progress beyond controls and programs by enabling businesses to identify cyber risks and take preventative action. There are two notable risk frameworks to consider: ISO 27005 and CIS Ram.
ISO 27005
ISO 27005 is an international standard that provides guidance on managing information security risks. It offers a structured approach to identifying, assessing, evaluating and treating information security risks.
It helps organisations understand and manage their risk exposure, ensuring that security controls are implemented effectively to protect sensitive information. Key aspects include:
- Risk assessment: ISO 27005 provides a structured approach to identifying, analysing and evaluating information security risks.
- Risk treatment: It helps organisations determine the appropriate risk treatment strategies, such as mitigation, acceptance, transfer or avoidance.
- Risk monitoring and review: It outlines processes for monitoring and reviewing information security risks on an ongoing basis.
- Risk communication: It emphasises the importance of effective communication of risk information to relevant stakeholders.
In short, it’s a systematic way to prioritise risks, allocate resources accordingly and make informed decisions about security investments.
ISO 27005 is particularly useful for organisations aiming to achieve ISO 27001 certification, as it provides a practical framework for implementing risk management processes.
By adopting ISO 27005, organisations can improve their overall security posture, reduce the likelihood of data breaches and enhance their ability to respond to security incidents.
CIS RAM
CIS RAM (Risk Assessment Method) is a comprehensive framework designed to help organisations assess and manage their information security risks. It provides a structured approach to implementing the CIS Controls and ensuring they align with specific needs and risk tolerance.
CIS RAM offers a flexible and customisable approach to risk assessment, allowing organisations to tailor the process to their unique circumstances. It involves several key steps, including:
- Identifying assets
- Assessing vulnerabilities
- Analysing threats
- Determining impact
- Evaluating existing controls
By following these steps, organisations can gain a clear understanding of their risk landscape.
Once the risks have been identified and assessed, CIS RAM helps organisations prioritize them based on their potential impact and likelihood of occurrence. This prioritisation enables you to allocate resources effectively and focus on addressing the most critical risks first.
CIS RAM also emphasises the importance of ongoing risk monitoring and management. As the threat landscape evolves, organisations must continually reassess their risk posture and update their security controls accordingly.
How do you choose the right framework?
When selecting a cyber security framework, there are many factors you need to consider, including:
- Organisational size and complexity: Smaller organizations may benefit from simpler frameworks like Cyber Essentials and CIS Controls, while larger organisations may require more comprehensive frameworks like CIS RAM or ISO 27001.
- Industry regulations and compliance requirements: Certain industries (such as healthcare and finance) have specific regulatory requirements that must be met. If these are strict, you should look at implementing more robust frameworks, like CIS RAM and ISO 27005.
- Organisational culture and maturity: The framework should align with any existing security policies you have, in line with your wider culture. You need to assess your capabilities to apply the framework successfully and choose one that is most likely to drive results.
Of course, you can choose to layer multiple frameworks. For example, CIS Controls works very well with Cyber Essentials and CIS RAM. Similarly, ISO 27001 and 27005 complement each other. You can also combine elements from different frameworks to create a hybrid approach that best suits your organisation’s requirements.
If you are new to cyber security and are looking for a simple way to protect your business adequately, without overwhelming resources, Cyber Essentials will likely be your best starting point.
If you want to know more about Cyber Essentials, including what you need to do to achieve it, the assessment process and how to get started, our ‘What is Cyber Essentials?’ blog will tell you everything you need to know.
