In today’s world of business, your staff have access to a range of devices beyond the traditional desktop PC. These devices may live on your premises, in your employees’ homes or on the go. These devices need to be covered as part of your IT security plan.
Mobile device management (MDM) refers to the centralised administration and control of mobile devices, such as smartphones, tablets, and laptops, within an organisation. It involves deploying, securing, monitoring, integrating and managing mobile devices, applications, and data.
MDM enables organisations to enforce security policies, configure settings, distribute applications and ensure compliance across a fleet of mobile devices. By doing so, you can optimise their functionality, security and productivity.
Device management has always been an important part of any IT department, whether to configure company owned devices or manage company data on user’s personal phones and laptops.
With remote working now the norm, it has become a necessity to have a solution that minimises the time it takes to configure new and existing devices. It should also give you confidence that, if devices are lost or stolen, your company data is secured and easily removed.
Microsoft Intune device management
Microsoft Intune is a cloud-based offering that incorporates mobile device management and mobile application management. It allows your organisation to have complete control of how your users access company resources, whilst providing streamlined deployment options for corporate devices.
Intune mobile device management and mobile application management (MAM) handle how devices, security and application data is handled. MDM and MAM should work together to provide a safe and secure device management solution.
Depending on whether you provide a managed device to your users or allow personal devices to access your data, Intune allows you to cover each scenario.
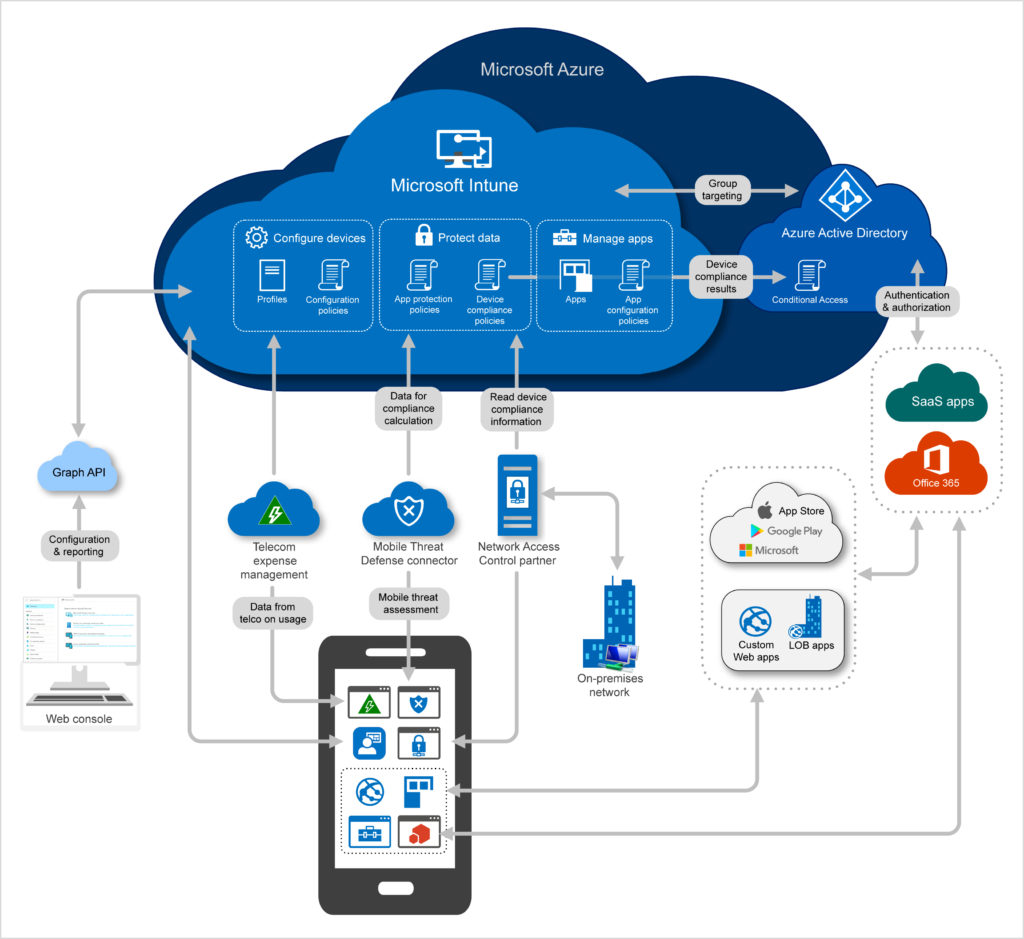
Enrolling devices
Enrolling devices into Microsoft Company Portal allows you to have full control over their settings, features and security.
With this approach, you can control how devices are configured via policies set within Intune. Once a device is enrolled, it will automatically pull its configuration from the cloud, allowing your users to have a seamless experience without needing to visit the office to collect their hardware.
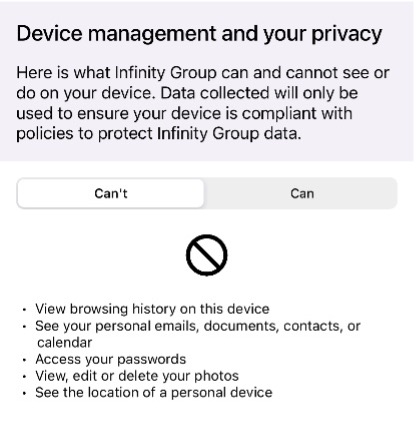
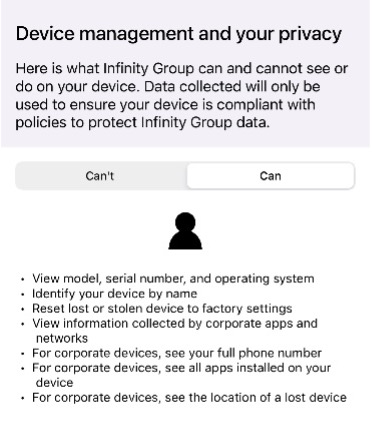
Devices can be allocated as corporately owned or personal. This will determine what visibility your IT department has into the device. Users can get an overview of what your IT department can see by accessing the company portal app on their device.
Here’s an example of device privacy:
Some examples of how a device can be configured include:
- System update policies, including feature updates to Windows 11
- Disk encryption, with BitLocker on Windows and FileVault on macOS
- Set PIN and password requirements
- Enable Windows Hello for Business
- Configure Wi-Fi and VPN connections
- Deploy security baselines
- Configure apps to automatically deploy based on users and groups
- Provide whitelisted apps that can be additionally installed based on user needs
- Easily reset or refresh devices to repurposes devices, or to lock misplaced devices
- Use conditional access policies, like automatically limiting device access to company resources should the device fail to be compliant with your policies
- Use autopilot, allowing devices to be sent directly from suppliers to users for a seamless out-of-box experience without IT support
Mobile application management
MAM policies allow you to protect your organisation’s data at the application level. This includes apps installed from Microsoft and third-party app stores, as well as custom apps you may have created for your team.
In this scenario, a user may not want their personal device to be managed by your company. But it is imperative that your company data is still protected. This can be achieved through app protection policies.
Some examples of how MAM can protect your data include:
- Isolate organisation data from personal data
- Configure apps to operate with specific settings enabled
- Require managed apps to be secured with a password
- Prevent copy and paste to apps outside of your control
- Prevent saving of documents to unmanaged apps
MDM and MAM should be used in conjunction with each other to provide the highest level of security. This enables personal devices to be used securely to access company resources.
Microsoft Intune licencing
Intune is included with the following Microsoft licences:
- Microsoft 365 E5
- Microsoft 365 E3
- Enterprise Mobility + Security E5
- Enterprise Mobility + Security E3
- Microsoft 365 Business Premium
- Microsoft 365 F1
- Microsoft 365 F3
- Microsoft 365 Government G5
- Microsoft 365 Government G3
- Intune for Education
If you are looking for mobile device management to help improve the performance and efficiency of your business, Infinity Group can help. As a specialist IT consultancy, our experts can make recommendations on how you can fully utilise mobile device management and level up security.
Please get in touch to discuss your needs.

